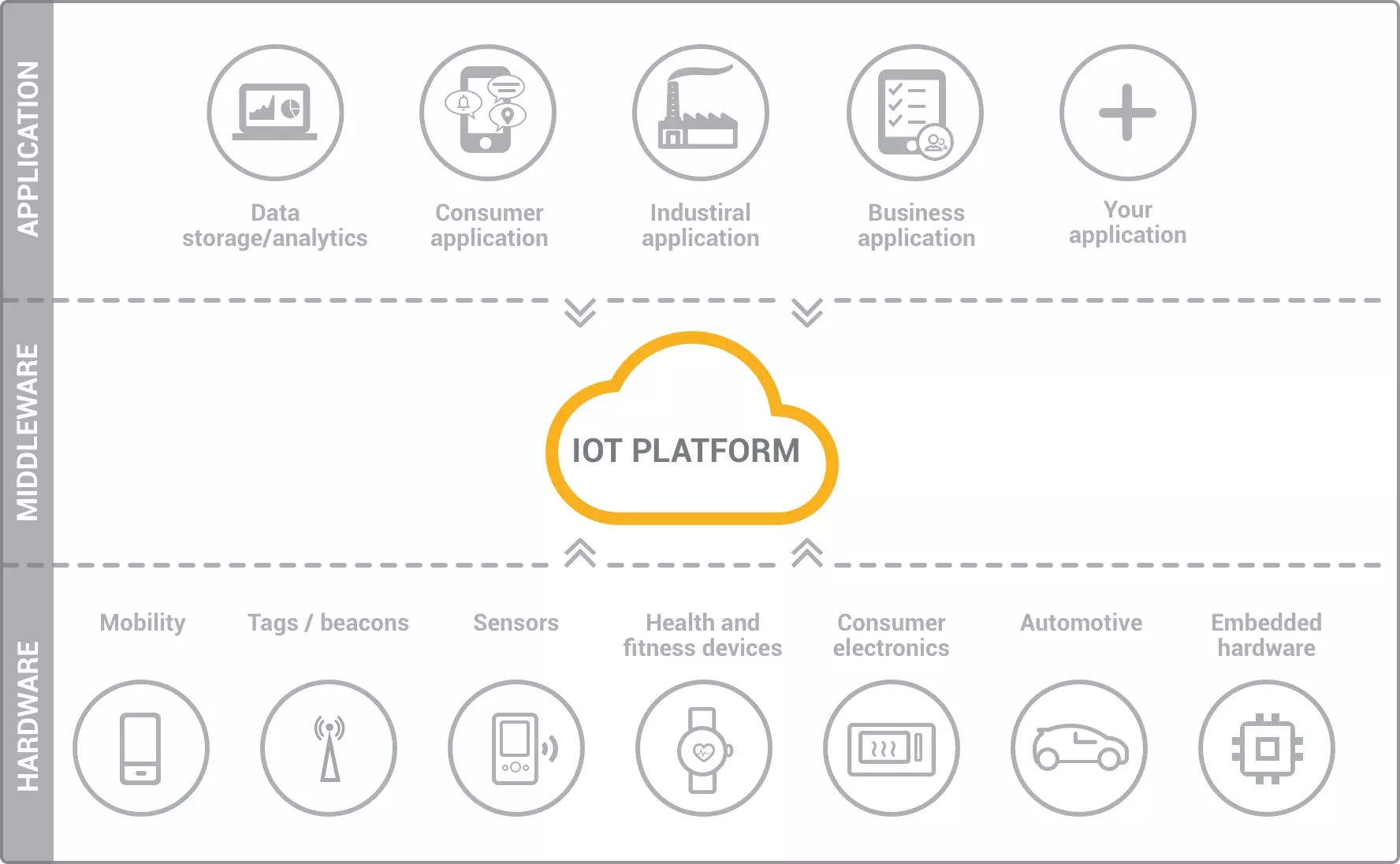
In today's interconnected world, managing Internet of Things (IoT) devices has become more crucial than ever. With the rapid expansion of IoT ecosystems, administrators and developers need robust methods to access and control these devices remotely. One of the most reliable approaches is through IoT SSH login CLI (Command Line Interface), which provides secure and efficient management capabilities. This article will explore the essential aspects of using SSH for IoT device management, offering expert insights and practical guidance to help you optimize your IoT infrastructure.
Understanding the fundamentals of IoT SSH login CLI is vital for anyone involved in managing connected devices. This method not only ensures secure remote access but also enables efficient configuration and troubleshooting. Whether you're a system administrator, IoT developer, or IT professional, mastering SSH CLI for IoT devices can significantly enhance your operational capabilities.
As we delve deeper into this topic, we'll cover everything from basic setup procedures to advanced security measures. You'll learn how to establish secure connections, manage multiple devices efficiently, and implement best practices for maintaining a robust IoT infrastructure. Let's explore how IoT SSH login CLI can transform your device management approach while adhering to the highest security standards.
Read also:Negan Actor Unveiling The Man Behind The Iconic Role
Table of Contents
Understanding IoT SSH Login CLI
IoT SSH login CLI represents a fundamental tool for managing connected devices across various industries. This method combines the security of Secure Shell (SSH) protocol with the efficiency of command-line interfaces, enabling administrators to interact with IoT devices remotely. Unlike traditional graphical user interfaces, CLI offers precise control and automation capabilities, making it particularly suitable for managing large-scale IoT deployments.
The core components of IoT SSH login CLI include:
- SSH Protocol: Provides encrypted communication channels
- Authentication Mechanisms: Ensures secure access through various methods
- Command Structure: Offers standardized commands for device management
- Session Management: Maintains persistent connections for efficient operations
Key Benefits of Using IoT SSH Login CLI
Implementing IoT SSH login CLI offers numerous advantages:
- Enhanced Security: Utilizes strong encryption and authentication protocols
- Improved Efficiency: Enables batch processing and automation
- Remote Accessibility: Facilitates device management from anywhere
- Resource Optimization: Minimizes bandwidth usage compared to GUI-based tools
Setup and Configuration Process
Establishing a functional IoT SSH login CLI environment requires careful planning and execution. The setup process typically involves several critical steps, starting from initial device configuration to establishing secure access protocols.
Initial Device Configuration
Before enabling SSH access, ensure your IoT devices meet the following requirements:
- Firmware version compatibility
- Network connectivity
- Administrative access privileges
Follow these steps for basic setup:
Read also:Christopher Scarver The Man Who Changed Prison History Forever
- Access device's administrative interface
- Enable SSH service in system settings
- Configure port settings (default: 22)
- Set up initial user credentials
Advanced Configuration Options
For enhanced functionality, consider implementing these advanced settings:
- Key-based authentication
- IP address restrictions
- Session timeout configurations
- Logging and monitoring parameters
Security Best Practices
Securing IoT SSH login CLI connections is paramount to protecting your infrastructure from potential threats. Implementing robust security measures ensures the integrity and confidentiality of your device management operations.
Authentication Security Measures
Enhance your authentication process through:
- Multi-factor authentication (MFA)
- Public key infrastructure (PKI)
- Password complexity requirements
According to recent cybersecurity reports, implementing MFA can reduce unauthorized access attempts by up to 99.9%.
Network Security Protocols
Implement these network security measures:
- Firewall rules for SSH traffic
- VPN integration
- Intrusion detection systems
Advanced Features and Capabilities
Modern IoT SSH login CLI implementations offer sophisticated features that enhance device management capabilities:
Automation and Scripting
Utilize scripting languages like Python or Bash to automate routine tasks:
- Batch configuration updates
- Scheduled maintenance operations
- Automated backups
Monitoring and Logging
Implement comprehensive monitoring solutions:
- Real-time performance tracking
- Event logging
- Alert notifications
Troubleshooting Common Issues
Addressing common challenges in IoT SSH login CLI operations requires systematic approaches:
Connection Problems
Common connection issues include:
- Firewall restrictions
- Incorrect port configurations
- Authentication errors
Solution strategies:
- Verify network settings
- Check firewall rules
- Validate authentication credentials
Performance Optimization
Enhance performance through:
- Connection pooling
- Session caching
- Command optimization
Efficient Device Management Strategies
Managing multiple IoT devices through SSH CLI requires strategic approaches:
Centralized Management
Implement centralized management solutions:
- Configuration management tools
- Device grouping
- Policy enforcement
Scalability Considerations
Plan for growth by:
- Implementing load balancing
- Designing modular architectures
- Establishing redundancy protocols
Automation and Scripting
Automation plays a crucial role in efficient IoT device management:
Scripting Languages
Popular scripting options include:
- Python with Paramiko library
- Bash scripts
- PowerShell
Automation Frameworks
Utilize established frameworks:
- Ansible
- Puppet
- Chef
Performance Optimization
Optimizing IoT SSH login CLI performance requires attention to several factors:
Connection Management
Implement efficient connection strategies:
- Keep-alive settings
- Connection pooling
- Session reuse
Resource Utilization
Monitor and optimize resource usage:
- CPU performance
- Memory allocation
- Network bandwidth
Future Trends in IoT SSH
The evolution of IoT SSH login CLI continues to shape device management practices:
Emerging Technologies
Key developments include:
- Quantum-resistant encryption
- AI-powered automation
- Edge computing integration
Industry Standards
Current standardization efforts focus on:
- Interoperability protocols
- Security certifications
- Performance benchmarks
Conclusion and Recommendations
Mastering IoT SSH login CLI is essential for effective device management in today's connected world. Throughout this article, we've explored the fundamental aspects of IoT SSH, from basic setup procedures to advanced security measures and performance optimization techniques. By implementing the strategies and best practices discussed, you can significantly enhance your IoT infrastructure's security, efficiency, and scalability.
To further improve your IoT device management capabilities, consider the following actions:
- Regularly update your SSH configurations
- Implement comprehensive monitoring solutions
- Explore automation frameworks for routine tasks
- Stay informed about emerging security threats
We encourage you to share your experiences with IoT SSH login CLI in the comments below. If you found this article helpful, please consider sharing it with your professional network. For more in-depth technical guides and industry insights, explore our other articles covering various aspects of IoT management and cybersecurity.