Accessing remote IoT devices within a Virtual Private Cloud (VPC) via SSH on Windows 10 can be a challenging task for many users. However, with the right tools and configurations, this process can become seamless and secure. Whether you are managing IoT devices, troubleshooting remote systems, or ensuring secure connections, understanding the steps to establish a reliable SSH connection is crucial. This article will guide you through the entire process, ensuring you can connect to your IoT devices efficiently and securely.
Remote access to IoT devices in a VPC is essential for maintaining operational efficiency and security. IoT devices, often deployed in remote locations, require constant monitoring and management. Using SSH (Secure Shell) ensures that your connection is encrypted, protecting sensitive data from unauthorized access. Windows 10, with its robust features, provides a versatile platform for managing these connections. However, the lack of native SSH tools in older versions of Windows has led many users to seek alternative solutions.
In this article, we will explore the best practices for setting up SSH connections to IoT devices within a VPC on Windows 10. We will cover everything from installing necessary tools to configuring your network for secure access. By the end of this guide, you will have a clear understanding of how to access your IoT devices remotely without complications. Let’s dive in!
Read also:Is Michael Boulos Muslim Or Christian Unraveling The Truth About His Religious Beliefs
Table of Contents
- Introduction to IoT, VPC, and SSH
- Essential Tools for SSH on Windows 10
- Setting Up an SSH Client on Windows 10
- Configuring Your VPC for Remote Access
- Connecting to IoT Devices via SSH
- Troubleshooting Common SSH Issues
- Securing Your SSH Connection
- Best Practices for Remote IoT Access
- Exploring Advanced SSH Features
- Conclusion and Next Steps
Introduction to IoT, VPC, and SSH
The Internet of Things (IoT) refers to a network of interconnected devices that communicate and exchange data over the internet. These devices range from smart home appliances to industrial sensors, all designed to improve efficiency and convenience. A Virtual Private Cloud (VPC) is a secure, isolated private cloud hosted within a public cloud. It allows users to run their applications and store data in a controlled environment, ensuring privacy and security.
Secure Shell (SSH) is a cryptographic network protocol used for secure data communication. It provides a secure channel over an unsecured network, making it ideal for remote access to IoT devices within a VPC. SSH ensures that all data transmitted between your local machine and the remote device is encrypted, protecting it from potential threats. By leveraging SSH, you can manage your IoT devices securely and efficiently.
Why Use SSH for IoT Access?
- Encryption: SSH encrypts all data, preventing unauthorized access.
- Authentication: SSH uses strong authentication methods to verify user identity.
- Flexibility: SSH supports various configurations, making it adaptable to different use cases.
Essential Tools for SSH on Windows 10
Windows 10 now includes a built-in SSH client, making it easier for users to establish secure connections without installing third-party software. However, additional tools can enhance your SSH experience and provide more advanced features. Below are some essential tools you can use for SSH on Windows 10.
Windows 10 Built-in SSH Client
The Windows 10 OpenSSH client is a lightweight and efficient tool for establishing SSH connections. It is included by default in recent versions of Windows 10, eliminating the need for external installations. To enable it, go to "Settings"> "Apps"> "Optional Features" and add the OpenSSH client.
Third-Party SSH Clients
- PuTTY: A popular SSH client with a user-friendly interface and advanced features like session management and key generation.
- MobaXterm: A comprehensive tool that combines SSH with other remote access utilities, such as X server and network tools.
- Bitvise SSH Client: Known for its robust security features and ease of use, ideal for managing multiple SSH connections.
Setting Up an SSH Client on Windows 10
Setting up an SSH client on Windows 10 is a straightforward process. Whether you choose the built-in OpenSSH client or a third-party tool, the steps are simple and intuitive. Below is a step-by-step guide to help you configure your SSH client.
Using the Built-in OpenSSH Client
- Open "Settings" and navigate to "Apps"> "Optional Features."
- Click "Add a feature" and search for "OpenSSH Client."
- Install the OpenSSH client and restart your computer if prompted.
- Open the Command Prompt or PowerShell and type
sshto verify installation.
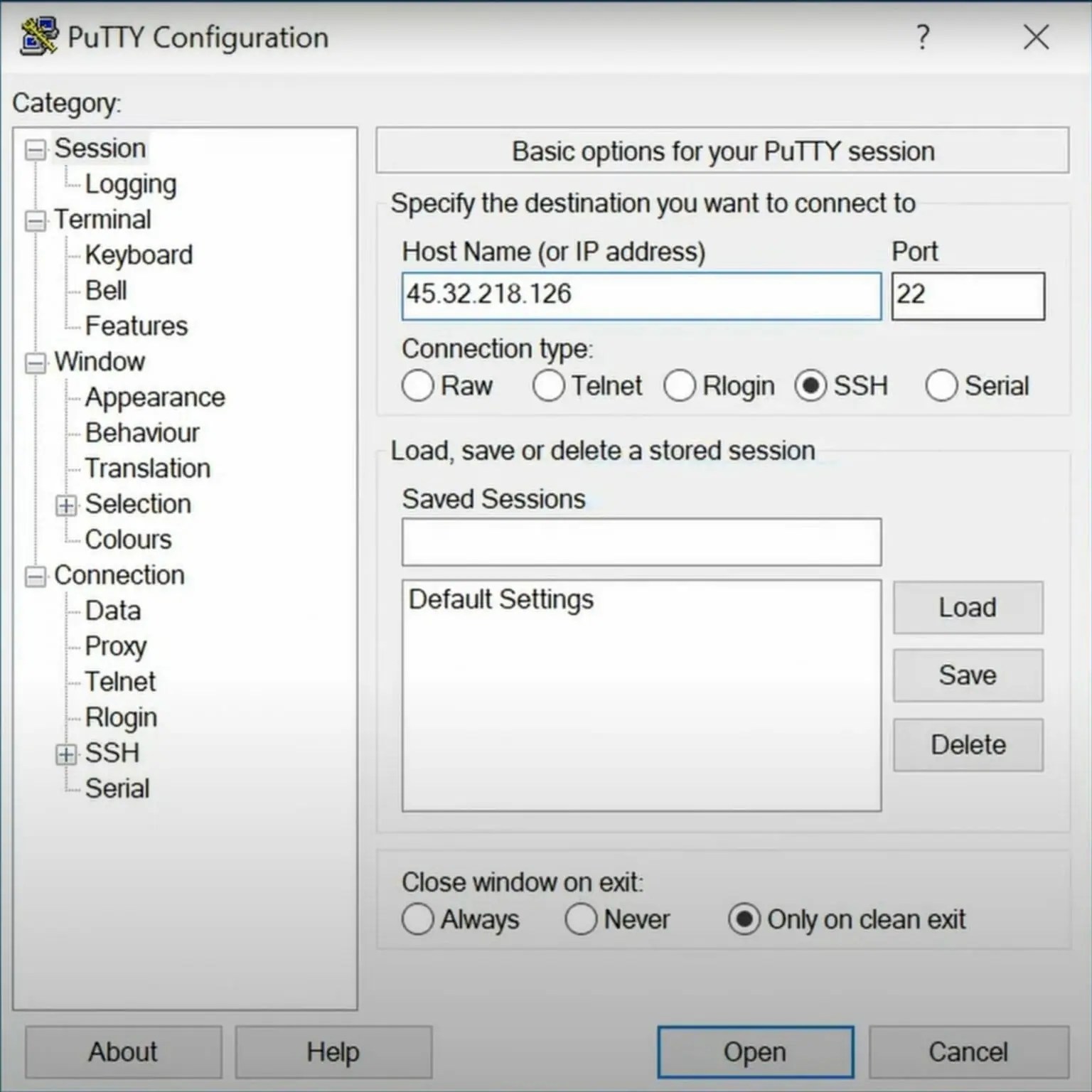
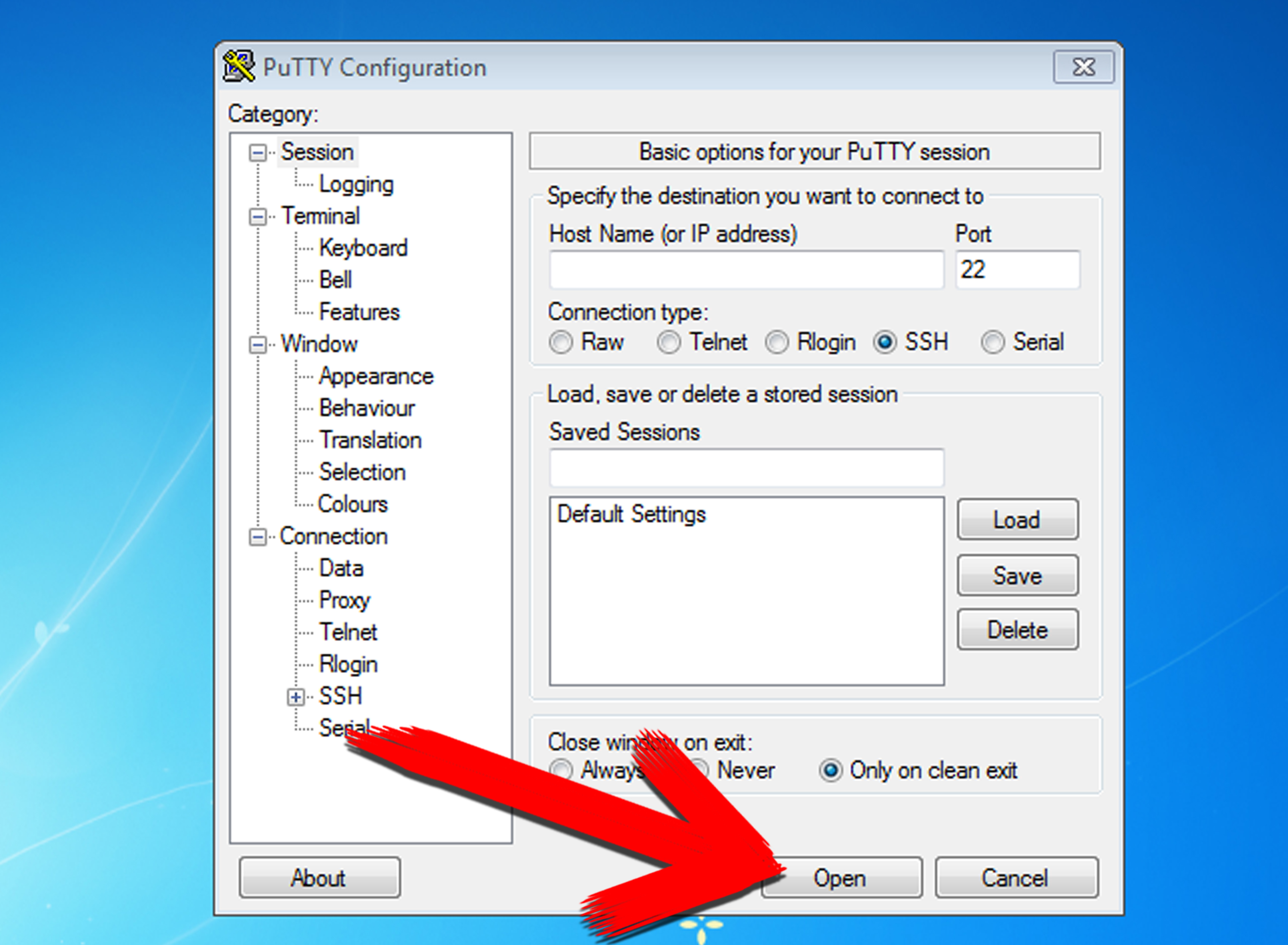
Configuring PuTTY for SSH
- Download and install PuTTY from its official website.
- Launch PuTTY and enter the IP address or hostname of the remote IoT device.
- Select "SSH" as the connection type and specify the port (default is 22).
- Click "Open" to initiate the connection and log in using your credentials.
Configuring Your VPC for Remote Access
Before establishing an SSH connection to your IoT devices, you need to configure your VPC to allow remote access. This involves setting up security groups, network access control lists (ACLs), and ensuring proper routing within the VPC.
Read also:Shahid Bolson A Rising Star In The World Of Entertainment
Setting Up Security Groups
Security groups act as virtual firewalls for your VPC, controlling inbound and outbound traffic. To allow SSH access:
- Log in to your cloud provider's management console (e.g., AWS, Azure).
- Navigate to the VPC dashboard and locate the security group associated with your IoT devices.
- Add an inbound rule to allow SSH traffic (port 22) from your IP address.
- Save the changes and verify the configuration.
Configuring Network ACLs
Network ACLs provide an additional layer of security by controlling traffic at the subnet level. Ensure that your ACLs allow SSH traffic by:
- Creating inbound and outbound rules for port 22.
- Specifying the source and destination IP addresses.
- Testing the configuration to confirm connectivity.
Connecting to IoT Devices via SSH
Once your VPC is configured, you can proceed to connect to your IoT devices using SSH. This section will guide you through the process of establishing a secure connection and managing your devices remotely.
Establishing an SSH Connection
To connect to an IoT device, follow these steps:
- Open your SSH client (e.g., OpenSSH, PuTTY).
- Enter the device's IP address or hostname.
- Specify the SSH port (default is 22).
- Authenticate using your username and password or SSH key.
Managing IoT Devices Remotely
Once connected, you can perform various tasks, such as:
- Updating firmware and software.
- Monitoring device performance and logs.
- Configuring settings and parameters.
Troubleshooting Common SSH Issues
While SSH is a reliable protocol, users may encounter issues such as connection failures, authentication errors, or slow performance. Below are some common problems and their solutions.
Connection Refused Error
This error occurs when the SSH service is not running on the remote device or the port is blocked. To resolve:
- Verify that the SSH service is active on the IoT device.
- Check the security group and ACL settings in your VPC.
- Ensure the correct port is specified in your SSH client.
Authentication Failed
If you receive an authentication error, ensure that:
- Your username and password are correct.
- Your SSH key is properly configured and associated with the device.
- The device's SSH configuration allows the authentication method you are using.
Securing Your SSH Connection
Securing your SSH connection is critical to protecting your IoT devices and data. Below are some best practices to enhance the security of your SSH setup.
Using SSH Keys Instead of Passwords
SSH keys provide a more secure authentication method compared to passwords. To set up SSH keys:
- Generate an SSH key pair on your local machine using tools like
ssh-keygen. - Copy the public key to the remote IoT device.
- Disable password authentication in the SSH configuration file on the device.
Changing the Default SSH Port
Changing the default SSH port (22) can reduce the risk of brute-force attacks. To change the port:
- Edit the SSH configuration file on the IoT device (usually located at
/etc/ssh/sshd_config). - Specify a new port number and restart the SSH service.
- Update your SSH client to use the new port.
Best Practices for Remote IoT Access
Managing remote IoT devices requires careful planning and adherence to best practices. Below are some recommendations to ensure smooth and secure operations.
Regularly Update Firmware and Software
Keeping your IoT devices up to date is essential for security and performance. Regular updates patch vulnerabilities and improve functionality.
Monitor Device Logs
Monitoring logs helps identify potential issues and ensures that your devices are functioning correctly. Use tools like syslog or cloud-based monitoring services.
Implement Network Segmentation
Segmenting your network isolates IoT devices from other systems, reducing the risk of unauthorized access. Use subnets and firewalls to enforce segmentation.
Exploring Advanced SSH Features
SSH offers several advanced features that can enhance your remote access experience. Below are some features worth exploring.
SSH Tunneling
SSH tunneling allows you to securely forward traffic between your local machine and the remote IoT device. This is useful for accessing web interfaces or databases securely.
Port Forwarding
Port forwarding enables you to redirect traffic from one port to another, facilitating access to services running on different ports.
SSH Multiplexing
SSH multiplexing allows multiple SSH sessions to share a single connection, improving performance and reducing latency.
Conclusion and Next Steps
Accessing remote IoT devices within a VPC via SSH on Windows 10 is a powerful capability that enhances security and operational efficiency. By following the steps outlined in this guide, you can establish secure connections, troubleshoot common issues, and implement best practices for managing your IoT devices. Remember to regularly update your tools and configurations to stay ahead of potential threats.
We encourage you to experiment with advanced SSH features and explore additional tools to optimize your remote access experience. If you found this article helpful, please share it with others and leave a comment below with your thoughts or questions. For more guides and resources, check out our other articles on IoT and cloud computing. Happy connecting!