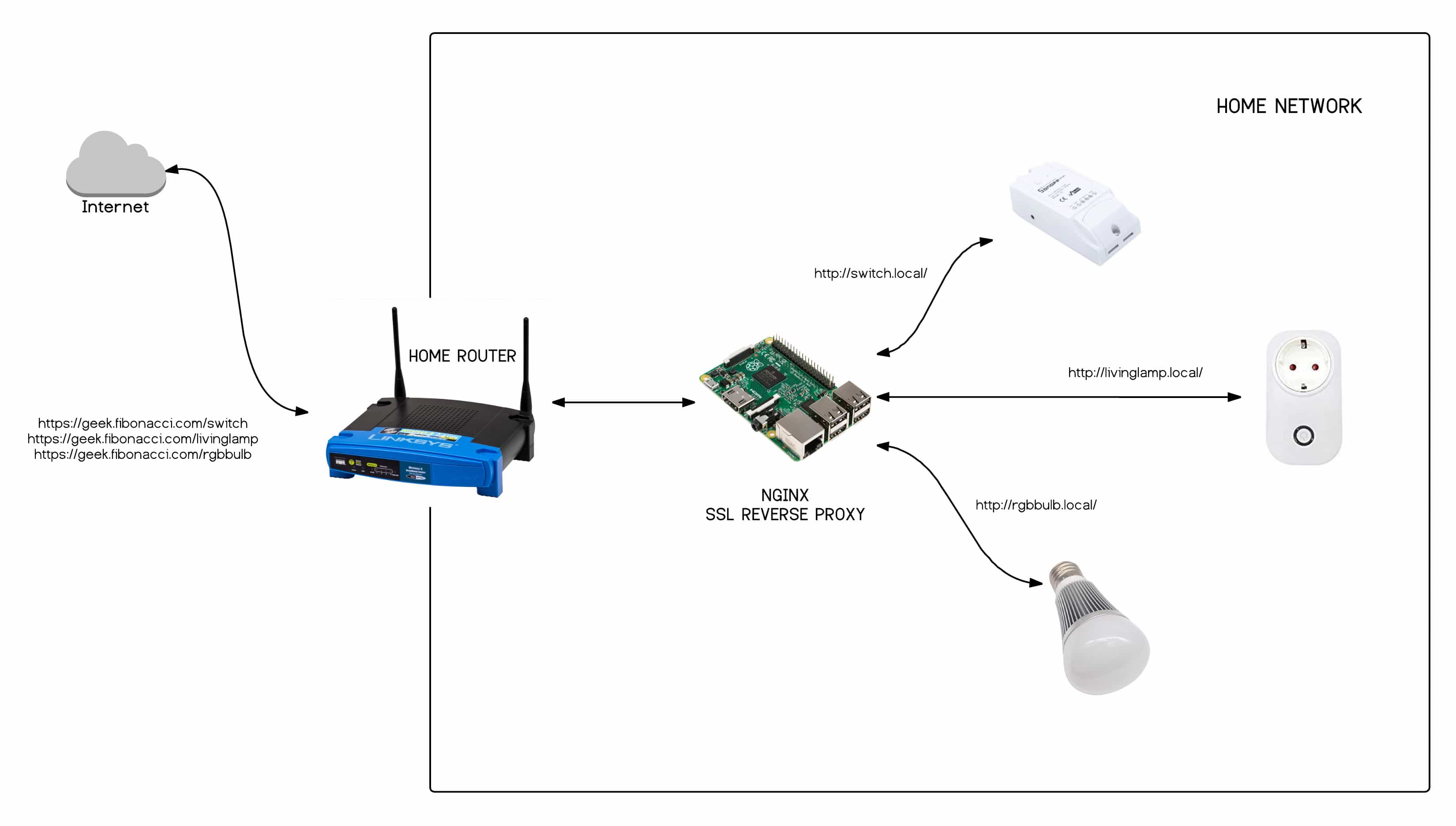
Remote SSH access for IoT devices has become a crucial aspect of managing and securing smart devices in today's interconnected world. With the rapid growth of IoT technology, users are increasingly seeking ways to access and control their devices remotely without incurring additional costs. This article will guide you through the process of enabling remote SSH access for IoT devices for free, ensuring secure and efficient management of your smart devices. Whether you're a beginner or an experienced user, this guide will provide you with actionable steps to enhance your IoT device management.
IoT devices are transforming industries and households, offering unparalleled convenience and automation. However, managing these devices remotely can be challenging, especially when it comes to security and accessibility. By enabling remote SSH access, you can gain full control over your IoT devices from anywhere in the world, ensuring they function optimally and securely. This guide will walk you through the tools, techniques, and best practices to achieve this without spending a dime.
In this article, we will cover everything you need to know about remote SSH access for IoT devices. From understanding the basics of SSH to exploring free tools and services, we will provide a comprehensive roadmap to help you set up secure remote access. Additionally, we will discuss the importance of adhering to security best practices to protect your devices from potential threats. By the end of this article, you will have the knowledge and tools to manage your IoT devices effectively and securely.
Read also:Understanding The Meaning Of Maksud Agadjani A Comprehensive Guide
Table of Contents
- What is SSH and Why is it Important for IoT Devices?
- Benefits of Enabling Remote SSH Access for IoT Devices
- Free Tools and Services for Remote SSH Access
- Step-by-Step Guide to Enable Remote SSH Access
- Security Best Practices for Remote SSH Access
- Common Challenges and How to Overcome Them
- Real-World Use Cases of Remote SSH Access for IoT
- Advanced Techniques for Managing IoT Devices via SSH
- Troubleshooting Common SSH Issues
- Conclusion and Call to Action
What is SSH and Why is it Important for IoT Devices?
SSH, or Secure Shell, is a cryptographic network protocol used for secure communication between two devices over an unsecured network. It provides a secure channel for data transmission, making it an essential tool for managing IoT devices. SSH encrypts all data exchanged between the client and the server, ensuring that sensitive information remains protected from unauthorized access.
For IoT devices, SSH is particularly important because these devices often operate in environments where security is a top priority. With remote SSH access, users can securely configure, monitor, and troubleshoot their IoT devices without being physically present. This capability is especially useful for managing devices in remote locations or for automating tasks that require real-time access.
How SSH Works
SSH operates on a client-server model, where the client initiates a connection to the server. The server authenticates the client using cryptographic keys or passwords, ensuring that only authorized users can access the device. Once the connection is established, all data exchanged between the client and server is encrypted, preventing eavesdropping or tampering.
- SSH uses public-key cryptography for authentication.
- Data is encrypted using algorithms like AES or ChaCha20.
- SSH supports multiple authentication methods, including password-based and key-based authentication.
Benefits of Enabling Remote SSH Access for IoT Devices
Enabling remote SSH access for IoT devices offers numerous benefits, particularly in terms of convenience, security, and efficiency. Below are some of the key advantages:
- Remote Management: Access and control your IoT devices from anywhere in the world.
- Enhanced Security: SSH encrypts all data, protecting it from unauthorized access.
- Automation: Automate tasks and configurations using scripts and commands.
- Cost-Effective: Free tools and services make it affordable to implement remote SSH access.
Use Case: Smart Home Automation
For example, in a smart home setup, remote SSH access allows homeowners to troubleshoot and update their IoT devices, such as smart thermostats or security cameras, without needing to be physically present. This capability not only saves time but also enhances the overall user experience.
Free Tools and Services for Remote SSH Access
Several free tools and services are available to enable remote SSH access for IoT devices. These tools are user-friendly and provide robust features to ensure secure and efficient management. Below are some of the most popular options:
Read also:Art Schlichter Daughters A Comprehensive Look Into Their Lives And Legacy
- Ngrok: A tool that creates secure tunnels to localhost, allowing remote access to IoT devices.
- OpenSSH: A widely-used open-source implementation of the SSH protocol.
- Termius: A free SSH client that supports remote access and key management.
- Port Forwarding: A technique to route external traffic to internal devices.
Comparison of Tools
| Tool | Key Features | Platform Support |
|---|---|---|
| Ngrok | Secure tunnels, easy setup | Windows, macOS, Linux |
| OpenSSH | Open-source, highly customizable | Linux, macOS |
| Termius | SSH key management, mobile app | Windows, macOS, Linux, iOS, Android |
Step-by-Step Guide to Enable Remote SSH Access
Enabling remote SSH access for IoT devices involves several steps, from setting up the device to configuring the necessary tools. Follow the steps below to get started:
Step 1: Install an SSH Server on Your IoT Device
Most IoT devices come with an SSH server pre-installed. If not, you can install one using package managers like APT or YUM. For example, on a Raspberry Pi running Raspbian, you can install OpenSSH using the following command:
sudo apt-get install openssh-server
Step 2: Configure the SSH Server
After installing the SSH server, you need to configure it to allow remote connections. Edit the SSH configuration file located at /etc/ssh/sshd_config and ensure the following settings are enabled:
- PermitRootLogin no
- PasswordAuthentication no
- PubkeyAuthentication yes
Step 3: Set Up a Free Tunneling Service
To access your IoT device from the internet, you need to set up a tunneling service like Ngrok. Download and install Ngrok, then create a tunnel to your device using the following command:
./ngrok tcp 22
Security Best Practices for Remote SSH Access
While remote SSH access offers numerous benefits, it also introduces potential security risks. To protect your IoT devices, follow these best practices:
- Use Strong Passwords: Avoid using default or weak passwords for SSH authentication.
- Enable Key-Based Authentication: Use SSH keys instead of passwords for added security.
- Limit Access: Restrict SSH access to specific IP addresses or networks.
- Regularly Update Software: Keep your SSH server and IoT device firmware up to date.
Common Challenges and How to Overcome Them
Setting up remote SSH access for IoT devices can sometimes be challenging. Below are some common issues and their solutions:
- Firewall Restrictions: Ensure that port 22 is open on your firewall to allow SSH traffic.
- Network Configuration: Use port forwarding to route external traffic to your IoT device.
- Device Compatibility: Verify that your IoT device supports SSH and has sufficient resources.
Real-World Use Cases of Remote SSH Access for IoT
Remote SSH access is widely used in various industries to manage IoT devices efficiently. Below are some real-world examples:
- Industrial Automation: Remote monitoring and control of machinery and sensors.
- Healthcare: Managing medical IoT devices for patient monitoring.
- Agriculture: Controlling irrigation systems and monitoring soil conditions.
Advanced Techniques for Managing IoT Devices via SSH
For users looking to take their IoT management to the next level, advanced techniques like scripting and automation can be incredibly useful. Below are some ideas:
- Automate Backups: Use SSH scripts to automate backups of IoT device configurations.
- Centralized Monitoring: Set up a centralized dashboard to monitor multiple IoT devices.
- Custom Commands: Create custom SSH commands for frequently performed tasks.
Troubleshooting Common SSH Issues
If you encounter issues while setting up remote SSH access, refer to the troubleshooting tips below:
- Connection Refused: Check if the SSH server is running and listening on the correct port.
- Authentication Failed: Verify your SSH keys or password and ensure they are correctly configured.
- Slow Performance: Optimize your network settings and reduce latency.
Conclusion and Call to Action
Enabling remote SSH access for IoT devices is a powerful way to enhance their functionality and security. By following the steps and best practices outlined in this article, you can manage your IoT devices efficiently and securely without incurring additional costs. Whether you're a beginner or an experienced user, the tools and techniques discussed here will help you take full control of your smart devices.
We encourage you to try out the free tools mentioned in this article and share your experiences in the comments below. If you found this guide helpful, don't forget to share it with others who might benefit from it. For more articles on IoT and technology, explore our website and stay updated with the latest trends and insights.